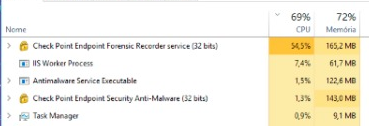
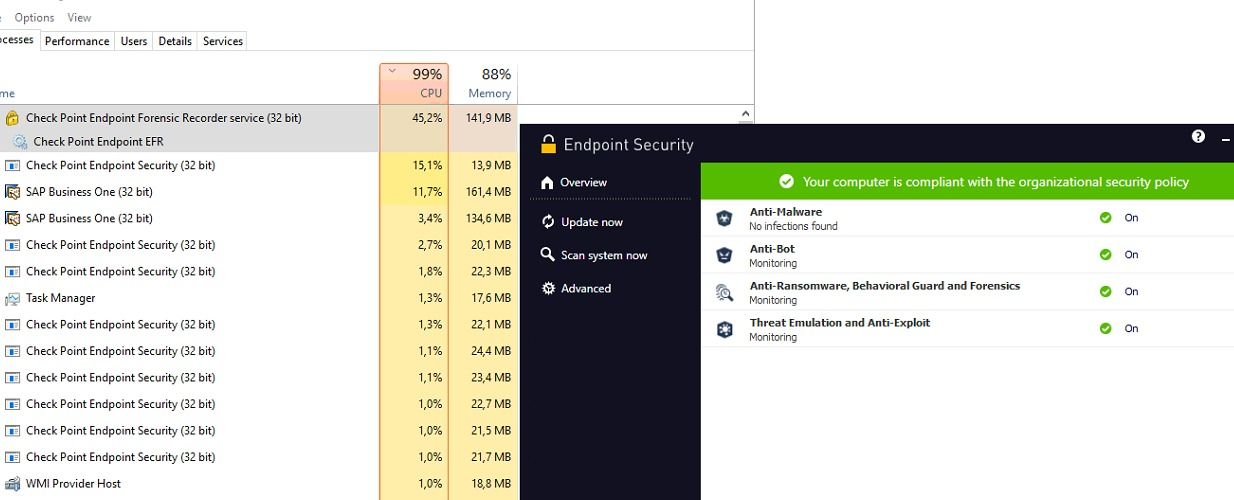
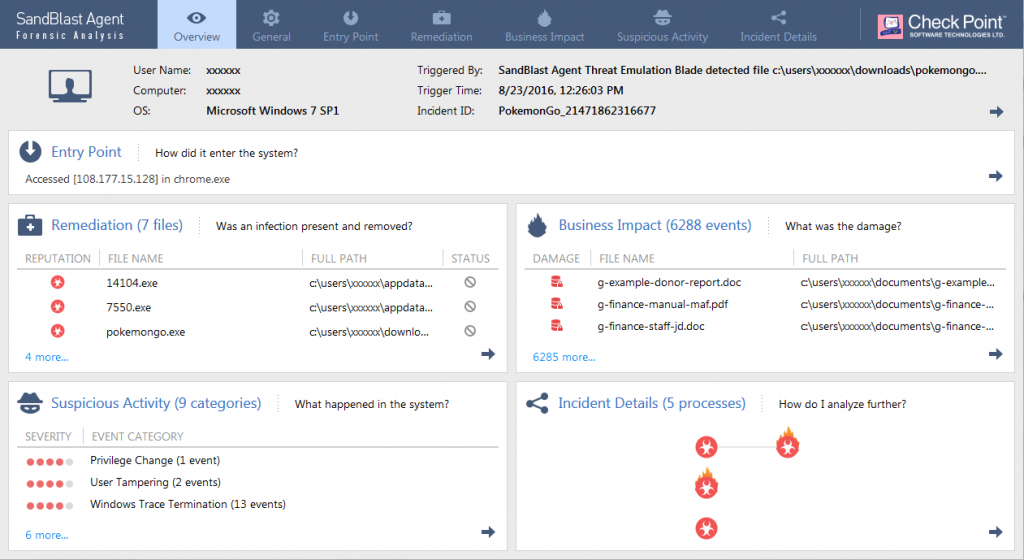
GitHub - mikeroyal/Self-Hosting-Guide: Self-Hosting Guide. Learn all about locally hosting (on premises & private web servers) and managing software applications by yourself or your organization. Including ChatGPT, WireGuard, Automation, Home Assistant ...

US9209995B2 - Presence status notification from digital endpoint devices through a multi-services gateway device at the user premises - Google Patents